In the rapidly evolving world of cryptocurrency, Cross-Chain bridges have emerged as pivotal technology enabling seamless transactions across disparate blockchains. This blog delves into the mechanics of these bridges, their vulnerabilities, and the implications for security in the decentralized finance landscape.
Table of Contents
- Introduction to Cross-Chain Transactions
- The Role of Trustless Bridges in DeFi
- Stablecoins: A Tool for Illicit Actors
- The FTX Case: A Recent Example
- Conclusion and Future Implications
Introduction to Cross-Chain Transactions
Cross-Chain transactions are essential in the multi-chain ecosystem of cryptocurrency. They enable the transfer of assets and data between different blockchain networks. As the cryptocurrency landscape becomes more fragmented, the need for efficient and secure Cross-Chain solutions grows.
Cross-Chain transactions allow users to access a broader range of decentralized applications (dApps) and services. This interconnectivity is crucial for promoting liquidity and innovation in the blockchain space.
The Rise of Blockchain Bridges
Blockchain bridges have surged in popularity as they facilitate Cross-Chain transactions. These bridges serve as conduits, allowing assets to move seamlessly between different blockchains. Their emergence has been driven by the increasing number of blockchain networks and the demand for interoperability.
As decentralized finance (DeFi) continues to expand, the role of bridges becomes even more critical. They not only enhance user experience but also contribute to the overall health of the cryptocurrency ecosystem.
Understanding the Bridge Ecosystem
The bridge ecosystem is diverse, consisting of various types of bridges that cater to different needs. Each bridge has its mechanisms for transferring value and information across blockchains. Understanding these differences is key to navigating the Cross-Chain landscape effectively.
Bridges can be categorized into two main types: centralized and decentralized. Centralized bridges rely on a trusted third party to manage transactions, while decentralized bridges utilize smart contracts to facilitate swaps autonomously.
Types of Blockchain Bridges
- Centralized Bridges: These bridges require users to deposit their assets with a central entity that manages the transfers. While they can offer faster transactions, they come with higher risks related to trust and security.
- Decentralized Bridges: These use smart contracts to automate transactions, providing a trustless environment. Users retain control over their assets, which enhances security but may involve longer transaction times due to network congestion.
- Wrapped Token Bridges: These bridges create wrapped versions of assets that can be used on different blockchains. This method mitigates volatility and allows for easier asset transfers across networks.
How Bridges Work: Mechanisms of Value Transfer
Bridges utilize various mechanisms to facilitate Cross-Chain transactions. The primary methods include locking, minting, and burning tokens.
- Lock and Mint: In this process, assets are locked in a vault on one blockchain, and an equivalent amount of new tokens is minted on the destination blockchain.
- Burn and Mint: Instead of locking assets, the original tokens are burned on one chain while new tokens are minted on the other. This method ensures that the total supply remains constant.
- Atomic Swaps: These allow for a direct exchange of assets between two parties without the need for a third party. This method enhances security and reduces the risk of fraud.
Case Study: The RenBridge Example
RenBridge is a prominent example of a Cross-Chain bridge that allows users to transfer assets between Ethereum and Bitcoin. It operates by wrapping tokens, creating RenBTC, which maintains a 1:1 value with Bitcoin.
In a typical transaction using RenBridge, a user deposits RenBTC into the bridge, which is then burned to create a corresponding amount of Bitcoin on the receiving side. This mechanism ensures that users can swap their assets without facing market volatility issues.
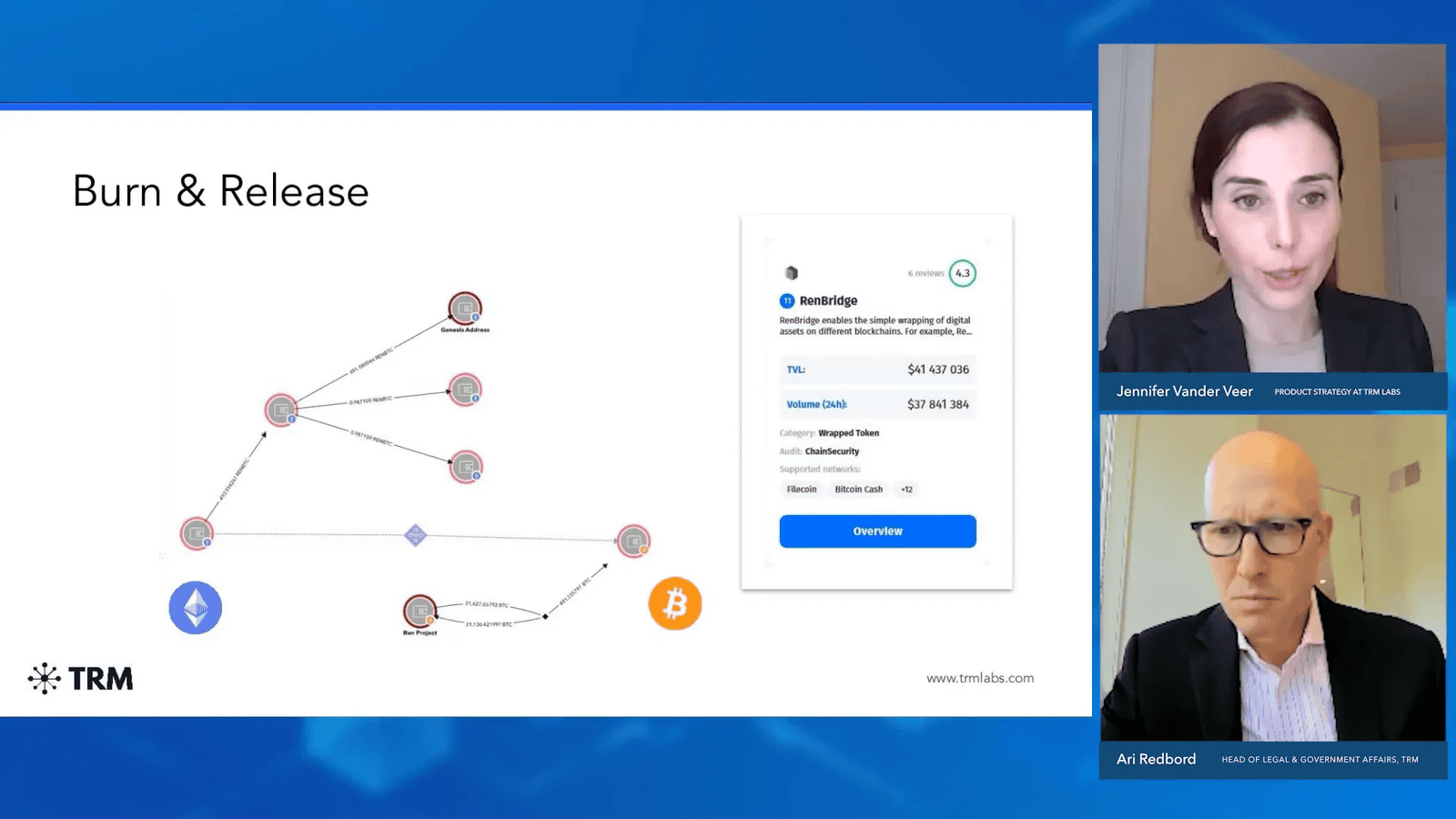
Additionally, the RenBridge example illustrates the importance of liquidity in the bridge ecosystem. To facilitate smooth transactions, a significant amount of cryptocurrency must be locked within the bridge’s vaults.
The increasing complexity of Cross-Chain transactions highlights the need for robust security measures. As bridges become more integral to the cryptocurrency landscape, they also attract the attention of malicious actors seeking to exploit vulnerabilities.
As the bridge ecosystem continues to evolve, understanding the dynamics of Cross-Chain transactions becomes crucial for users and developers alike. The rise of blockchain bridges signifies a pivotal shift towards a more interconnected and versatile cryptocurrency landscape.
The Role of Trustless Bridges in DeFi
Trustless bridges are fundamental to the decentralized finance (DeFi) ecosystem, facilitating seamless transactions between different blockchain networks. Their ability to eliminate the need for intermediaries represents a significant advancement in how users can manage and transfer assets across various platforms.
By utilizing smart contracts, these bridges allow users to interact with multiple blockchains without sacrificing security. This trustless environment is crucial for maintaining user confidence and encouraging broader participation in the DeFi space.
The efficiency of trustless bridges enhances liquidity across blockchains, enabling users to access a wider variety of financial services and products. This interconnectedness is vital for the growth of DeFi, as it allows users to optimize their asset management strategies while minimizing transaction costs.
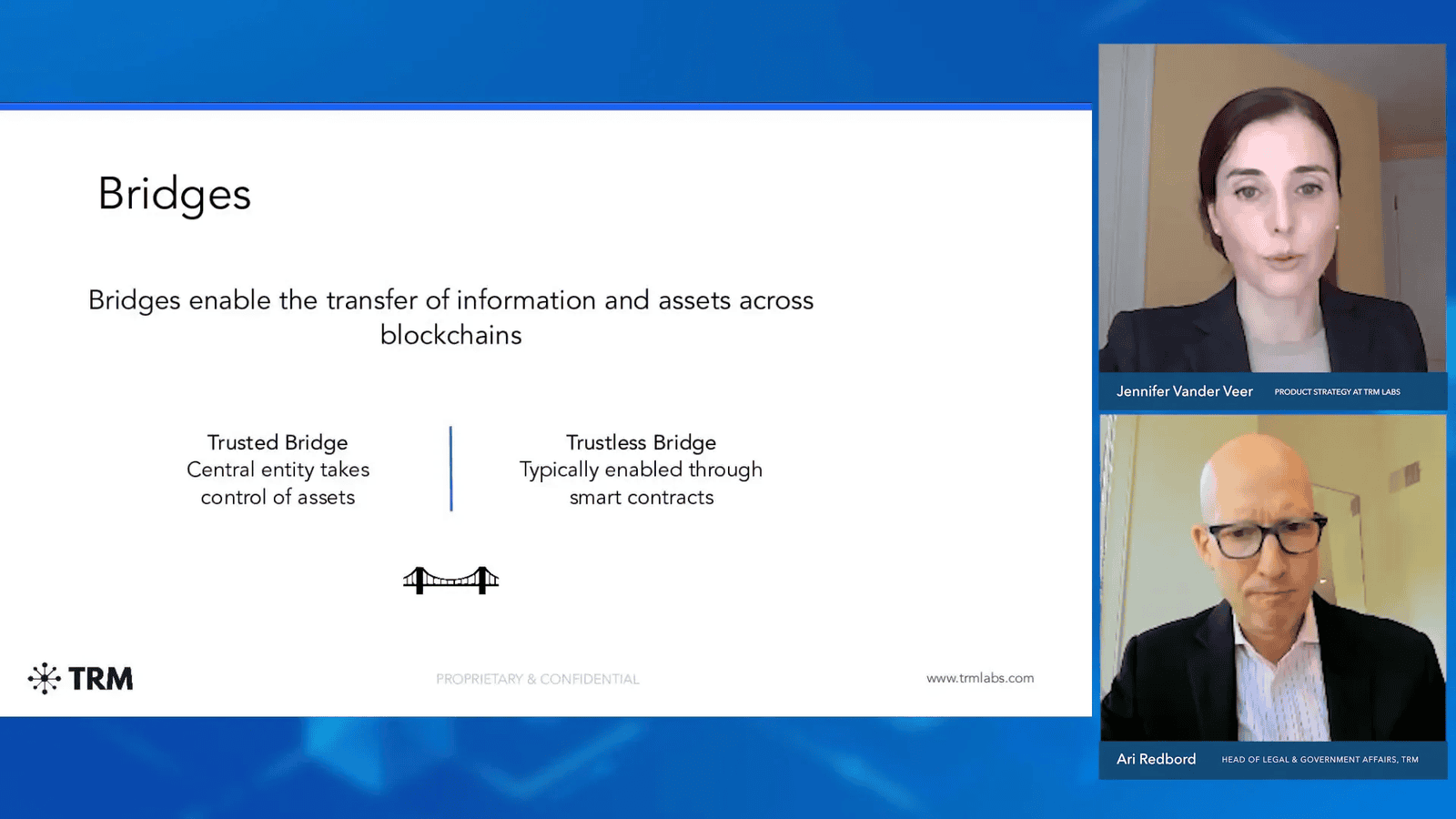
Illicit Activity and Exploits Targeting Bridges
Despite their advantages, trustless bridges have become attractive targets for illicit activities. Their role as conduits for asset transfer makes them a prime focus for hackers and other malicious actors seeking to exploit vulnerabilities within the blockchain ecosystem.
As the volume of transactions increases, so does the opportunity for illicit actors to engage in fraud and theft. The decentralized nature of these bridges can complicate tracking efforts, making it easier for bad actors to hide their tracks.
Understanding the motivations behind these attacks is essential for developing effective security measures. By analyzing historical incidents, we can identify patterns and vulnerabilities that need to be addressed to enhance the overall security of bridge infrastructure.

Analyzing the Ronin Bridge Hack
The Ronin Bridge hack, which resulted in the theft of approximately $600 million, exemplifies the vulnerabilities inherent in bridge technology. This incident was primarily caused by a private key compromise, allowing attackers to access the bridge’s funds due to the poor security of key management practices.
In this case, the attackers were able to obtain five out of the nine keys needed to authorize transactions. This highlights a critical issue: the reliance on a limited number of keys for controlling access to significant funds. When security measures are not adequately enforced, it becomes easier for malicious actors to exploit weaknesses.
Moreover, the Ronin Bridge hack underscores the importance of regular security audits and improved key management practices. By implementing more robust security protocols, bridge operators can significantly reduce the risk of similar incidents occurring in the future.
Vulnerabilities in Bridge Security
Bridges face various vulnerabilities that can be exploited by malicious actors. The most common types of attacks include smart contract exploits, private key compromises, and infrastructure attacks. Each type presents unique challenges for maintaining security.
- Smart Contract Exploits: These occur when attackers identify vulnerabilities in the code that governs the bridge. By exploiting these weaknesses, they can manipulate transactions or gain unauthorized access to funds.
- Private Key Compromises: Attackers may attempt to steal the keys that control the bridge, allowing them to bypass security measures and withdraw funds at will. This was the method used in the Ronin Bridge hack.
- Infrastructure Attacks: These attacks target the infrastructure surrounding the bridge, such as phishing schemes or DNS attacks, to gain access to sensitive information or disrupt operations.
Addressing these vulnerabilities requires a multi-faceted approach, including rigorous code audits, improved key management practices, and enhanced infrastructure security. By understanding the potential threats, bridge operators can implement measures to protect their systems.
Tracing Funds Across Blockchains
Tracing funds across blockchains is a critical aspect of maintaining security within the bridge ecosystem. As illicit actors increasingly use these bridges for money laundering and other nefarious activities, effective tracing becomes essential for regulators and law enforcement agencies.
Advanced tracking technologies can help identify patterns in fund movement, making it possible to follow the trail of illicit transactions. By monitoring Cross-Chain interactions, investigators can gain insights into the behavior of bad actors and potentially recover stolen assets.
The ability to trace funds is not only vital for law enforcement but also for building trust among users in the DeFi space. By demonstrating that effective tracking mechanisms are in place, bridge operators can enhance user confidence and deter illicit activities.
Illicit Use of Bridges for Money Laundering
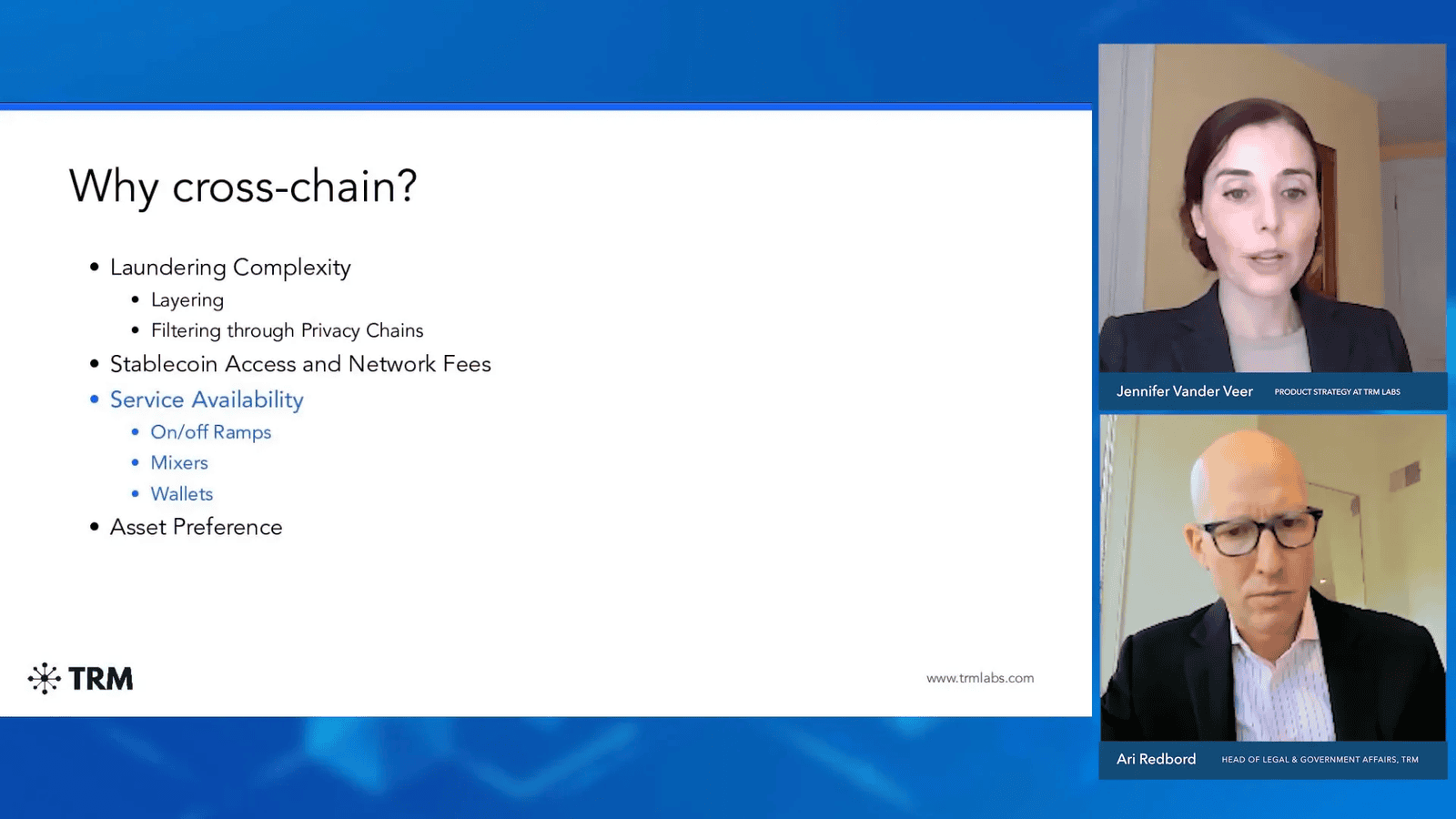
Bridges are increasingly being exploited for money laundering activities. By allowing the movement of assets across multiple blockchains, these bridges create opportunities for bad actors to obscure the origins of their funds.
One common tactic involves transferring funds through a series of different blockchains, effectively breaking the transaction history and complicating the tracing process. This layering of transactions adds complexity to the money laundering process, making it more challenging for authorities to detect and trace illicit funds.
For example, attackers may use bridges to funnel funds from a public blockchain into a privacy-focused blockchain, such as the Secret Network. Once the funds are in a more private environment, tracking becomes significantly more difficult, allowing the perpetrators to launder their assets with greater ease.
In conclusion, the role of trustless bridges in the DeFi landscape is undeniable. They facilitate Cross-Chain transactions, enhance liquidity, and promote innovation. However, they also present significant security challenges that must be addressed to protect users and maintain the integrity of the ecosystem.
Stablecoins: A Tool for Illicit Actors
Stablecoins have become a preferred asset for illicit actors seeking to launder funds. Their stability and wide acceptance across various blockchains make them an ideal choice for hiding and moving illicit gains.
By converting stolen assets into stablecoins, criminals can mitigate the risks associated with market volatility. This conversion often occurs through Cross-Chain bridges, allowing for rapid movement and obfuscation of the original asset’s trail.
For example, Tether (USDT) is frequently used due to its presence on numerous blockchains and relatively low transaction fees. As transaction costs rise on certain networks, illicit actors shift their funds to blockchains with lower fees, optimizing their laundering processes.
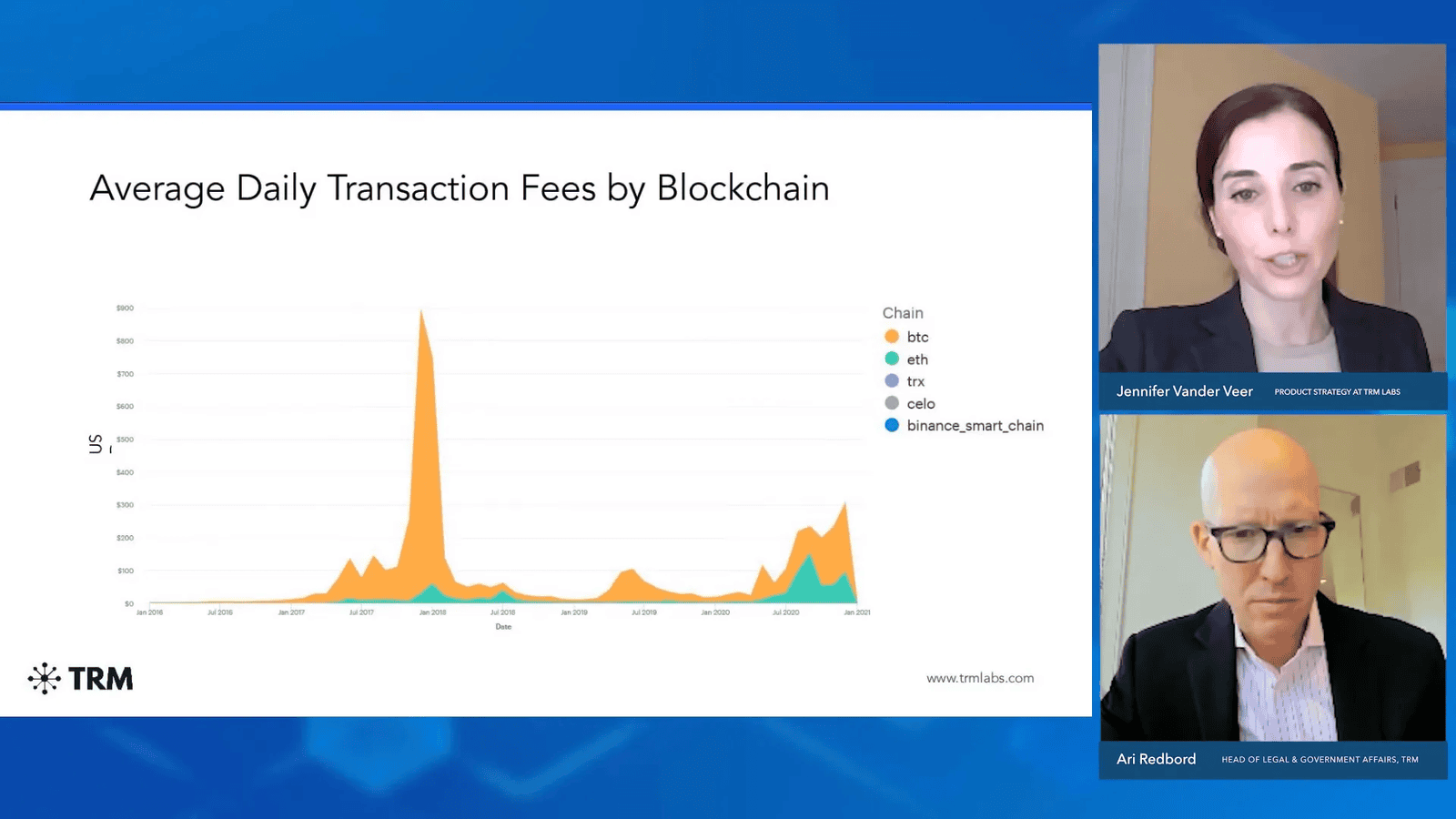
Service Availability and User Preferences
Service availability plays a significant role in the choices made by illicit actors. For instance, the shutdown of Tornado Cash, a popular Ethereum mixer, has led many to seek alternative mixing services primarily available on Bitcoin.
This shift not only enhances the anonymity of transactions but also allows actors to blend their funds more effectively. The availability of specific wallets and exchanges on different blockchains further influences these decisions, compelling users to move assets where services are accessible.
Moreover, user familiarity with certain blockchains can dictate preferences. Just as a diner might return to a favorite restaurant, illicit actors gravitate towards the blockchains they trust and understand.
The FTX Case: A Recent Example
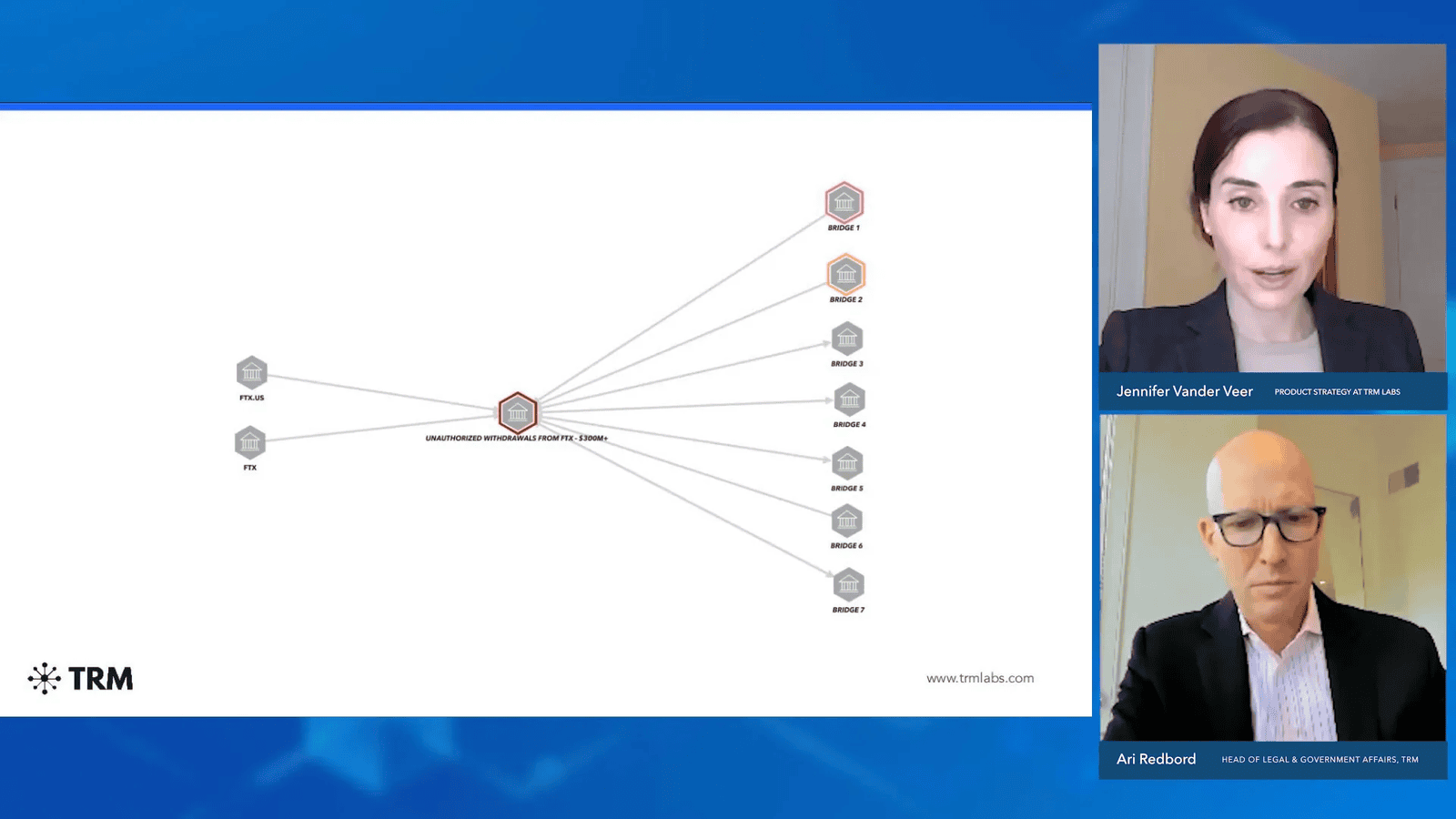
The FTX case serves as a critical example of how Cross-Chain bridges can be exploited during high-stakes financial crises. With over $300 million in unauthorized withdrawals, the movement of funds through various bridges has come under scrutiny.
Investigators noted that at least seven different bridges were involved in the transfer of these funds. This complexity highlights the challenges faced when tracing illicit transactions across multiple blockchains.
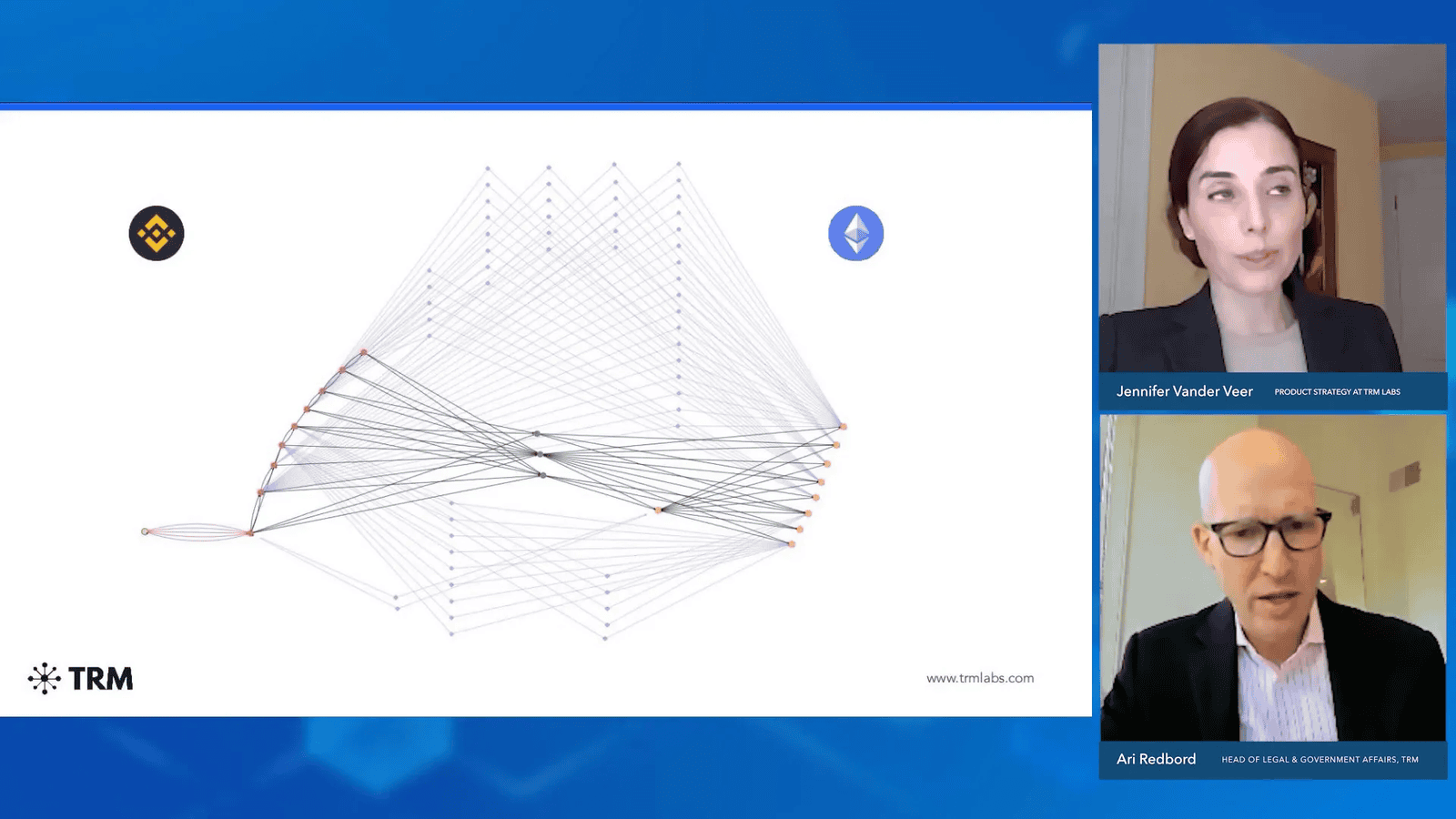
For instance, funds withdrawn from FTX on the Solana blockchain were traced through the Wormhole bridge to Ethereum. Tools like TRM can simplify this process, but the inherent complexity of Cross-Chain transactions remains a significant hurdle for investigators.
Comparing Bridges and Centralized Exchanges
When evaluating the differences between Cross-Chain bridges and centralized exchanges, several factors come into play. Unlike centralized exchanges, which often require extensive user verification and compliance measures, bridges typically operate with less oversight.
This lack of regulation can make bridges appealing for illicit activities. Users can swap assets with minimal information, avoiding the stringent KYC and AML protocols that govern centralized exchanges.
However, this poses challenges for law enforcement, as tracing transactions can become more complicated without the required compliance data. As the regulatory landscape evolves, the distinction between these two types of platforms will continue to blur, necessitating a reevaluation of compliance practices in the decentralized finance space.
Conclusion and Future Implications
The future of Cross-Chain bridges and their implications for the cryptocurrency landscape are significant. As more blockchains emerge, the interconnectedness of these systems will continue to grow, providing both opportunities and challenges.
Illicit actors will likely exploit these advancements to further their activities, necessitating enhanced tracking and regulatory measures. The ongoing evolution of decentralized finance demands that both users and regulators remain vigilant.
As the ecosystem matures, a balance must be struck between fostering innovation and ensuring security. Understanding the dynamics of Cross-Chain transactions will be crucial for stakeholders moving forward.